
Powerful data privacy and enhanced productivity for a leading KPO service provider
One of India’s largest BPO/KPO organizations needed to ensure the security of the highly sensitive healthcare data under their management.
Gain unified visibility and control over all Android and iOS devices through a centralized dashboard. Automate enrollment, approvals, and policy enforcement to ensure secure, consistent, and compliant device usage across your organization.
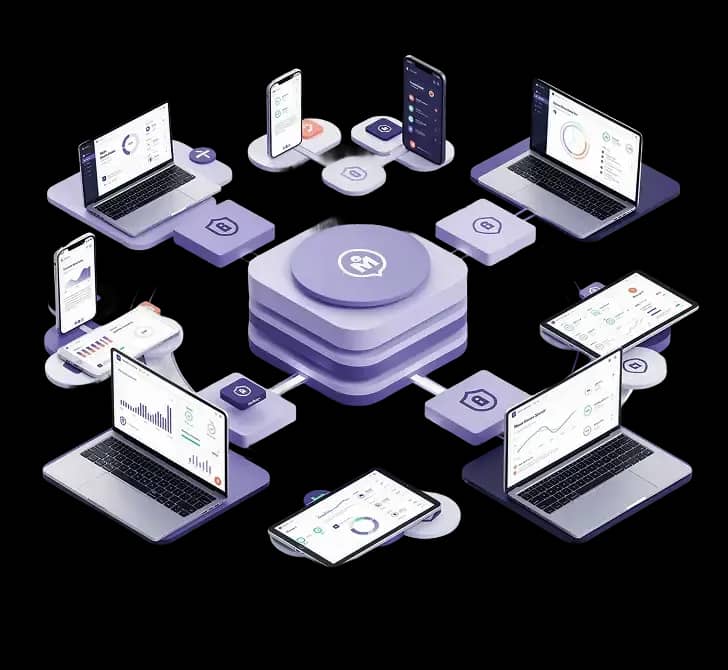
Mobile Device Management (MDM) allows organizations to centrally configure, monitor, and secure mobile devices - typically, smartphones and tablets - used by their employees. Rather than managing each device individually, MDM provides one place to enforce policies, protect corporate data, and maintain compliance across all mobile endpoints.
Akku delivers this capability through cloud-based controls that oversee device enrollment, restrict risky actions, isolate work data, and maintain secure configurations across both corporate-owned and BYOD devices.
Protect corporate information by separating work data from personal data on Android devices. Enforce secure Work Profiles that keep business apps and files contained, with clear boundaries that prevent cross-profile data movement or accidental data exposure

Ensure users only access trusted and approved applications on their mobile devices. Enable complete app governance with whitelisting, policy-based permissions, and the deployment of private or custom apps for internal use.
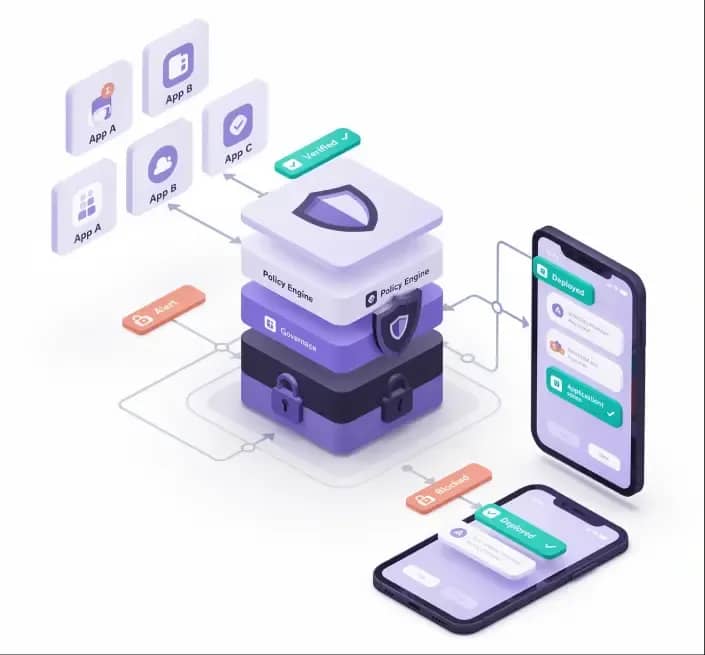
Respond quickly to lost, stolen, or compromised devices by removing work data without affecting personal content. Implement fast, remote actions to secure accounts and ensure sensitive information does not leave your organization.

Maintain strong device hygiene by enforcing critical security requirements across mobile endpoints. Enforce policies to govern passcodes, screen capture, and peripheral usage to ensure only compliant devices access corporate resources.

Apply fine-grained MDM policies based on organizational units (OUs) and maintain clear visibility into device compliance. Harness real-time reporting to help administrators track adherence to security standards and identify risks quickly.
