Powerful data privacy and enhanced productivity for a leading KPO service provider
One of India’s largest BPO/KPO organizations needed to ensure the security of the highly sensitive healthcare data under their management.
Define the conditions under which users and groups can access your organization’s apps and data with Akku’s contextual access control. Reinforce security by continuously checking these context signals before granting or maintaining access.
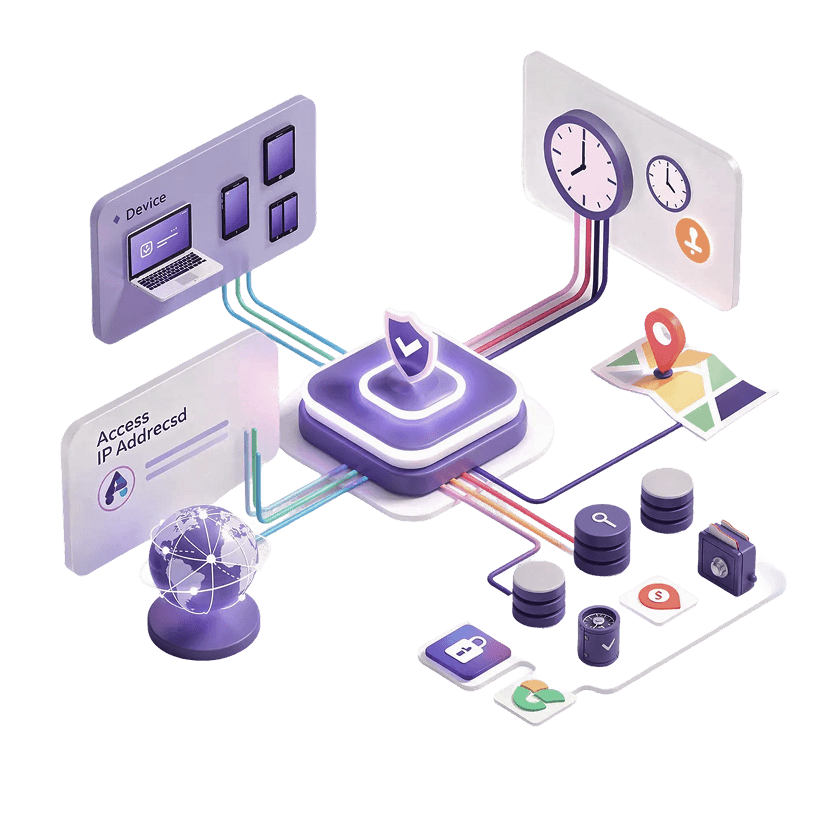
Contextual access control is a security approach where user access is granted or denied based on real-time context - such as where the user is connecting from, which device is used, when access is requested, and other risk indicators. Instead of static rules, it applies adaptive policies that change depending on risk level, helping enterprises secure modern, distributed work environments.
Empower administrators to create whitelists of approved IP addresses, restricting access to your organization’s applications solely to authorized locations such as offices or users' homes. Ensure that users can only access apps and data from approved locations, enhancing security and control over access privileges.
Ensures that only devices registered against a specific user profile can access that user's account by utilizing Akku’s agent to collect the serial number and BIOS UUID from each user’s device, and associating these details with the user profile. Restrict access from unrecognized devices with Akku verifying both user and device details during login attempts.
Give your administrators the ability to set specific time intervals for restricting access. Ensure that access to your organization's applications is only permitted during designated time periods, and restrict access outside of these predefined times to enhance security.
Automate real-time and scheduled bi-directional data syncs across multiple directories with built-in conflict resolution, ensuring consistent user information and immediate propagation of changes.

Put high‑risk or non-compliant users and devices into a restricted access zone where they can only access limited resources until they meet security requirements.